With the RiskNow platform
easily comply with
ISO27001
& SOC2
With the RiskNow SaaS-platform, you can easily achieve ISO27001-certification and SOC2-reporting within 6 months.


Save time and money with an integrated approach
By choosing an integrated approach, you save time and money. Do you want to obtain an ISO27001 certificate first and then a SOC2-report? That is possible, we’ll ensure that the control framework is immediately “SOC2-ready”.
Of course you can also choose for only ISO27001 or only SOC2.
Bye bye complexity
Information security is sometimes made unnecessarily complex by entering a lot of paperwork. At RiskNow, the management cycle is central (plan do-check-act). All important steps are recorded in RiskNow including:
- Risk analyses
- Controls
- Audits / Reviews
- Issues
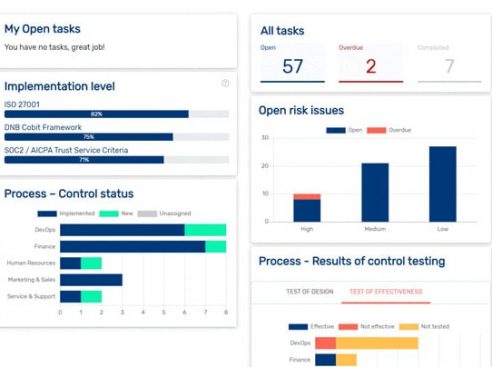

Compliance overviews
Overviews and reports provide a quick insight into the extent to which you comply with ISO27001 / ISO27002 / SOC2 (AICPA Trust Service Criteria)

Clear tasks, owners and deadlines
With RiskNow you set clear tasks, owners and deadlines. As a Risk, Security or Compliance Manager, you can see at a glance who should do what.
RiskNow Consultants en Auditors
RiskNow has a large network of experienced consultants and auditors who can support you with your ISO27001 / SOC2 project.
Security Officer-as-a-Service
As part of ISO27001/SOC2, it is important that internal audits review are performed on information security. This responsibility is often assigned to the Security Officer. If you do not have a Security Officer in your organization, you can also (temporarily or permanently) use our Security Officer-as-a-Service. This allows you to acquire knowledge and capacity without having to immediately appoint a full-time employee.
ISO27001-reference control areas

A.5 – Information Security Policies
Concerning information security measures as part of business continuity management.

A.6 – Organisation of Information Security
Concerning measures regarding the organisation of information security.

A.7 – Human Resource Security

A.8 – Asset Managements
Concerns measures regarding inventory, ownership and return of (information) assets.

A.9 – Access Controls
Concerns security measures such as user management, authentication and periodic reviews on user access and permissions.

A.10 – Cryptography
Concerns measures related to encryption and key management.

A.11 – Physical & Environment Security
Concerns measures aimed at physical protection against external threats and physical access protection.

A.12 – Operations Security
Concerns measures aimed at operational security such as change management, capacity management, separations between environments, measures aimed at malware, backups, logging and monitoring and vulnerability management.

A.13 – Communications Security
Concerns measures aimed at securing information flows between systems and on networks.

A.14 – System Acquisition, Development & Maintenance
Concerns measures aimed at purchasing systems, (secure) development and maintenance of systems.

A.15 – Supplier Relationships

A.16 Information Security Incident Management
Concerns measures aimed at dealing with information security incidents.

A.17 – Information Security Aspects of Business Continuity Management
Concerning information security measures as part of business continuity management.

A.18 – Compliance
Concerns measures to monitor compliance with policy, relevant legislation and regulations and contract agreements.
Lees ook onze blog post
“Best practices ISO27001 en SOC2”
SOC2 / Trust Service Criteria

Security

Availability

Confidentiality

Processing Integrity

Privacy
Interested?
Contact us for a no-obligation conversation or request a 30-day free trial.
